Open Source Security and Cost Management
Putting you in control of managing risk in your infrastructure. From insider threats to eliminating human errors, don’t change how your staff works, accommodate them and be safer, secure, and flexible.
Sentrius is a single pane of glass application that enables you to secure your infrastructure and actors within your ecosystem. Deployed in K8s, Sentrius consists of an API server, integration proxy that acts as an interconnect between humans, agents, and services to third party tools. This enables us to limit key exposure and secure your infrastructure.
Sentrius combines a novel Zero Trust API that is always on and can be applied anywhere. Cryptographic Zero Trust Access Tokens that are AI assisted allow full control and true Zero Trust.
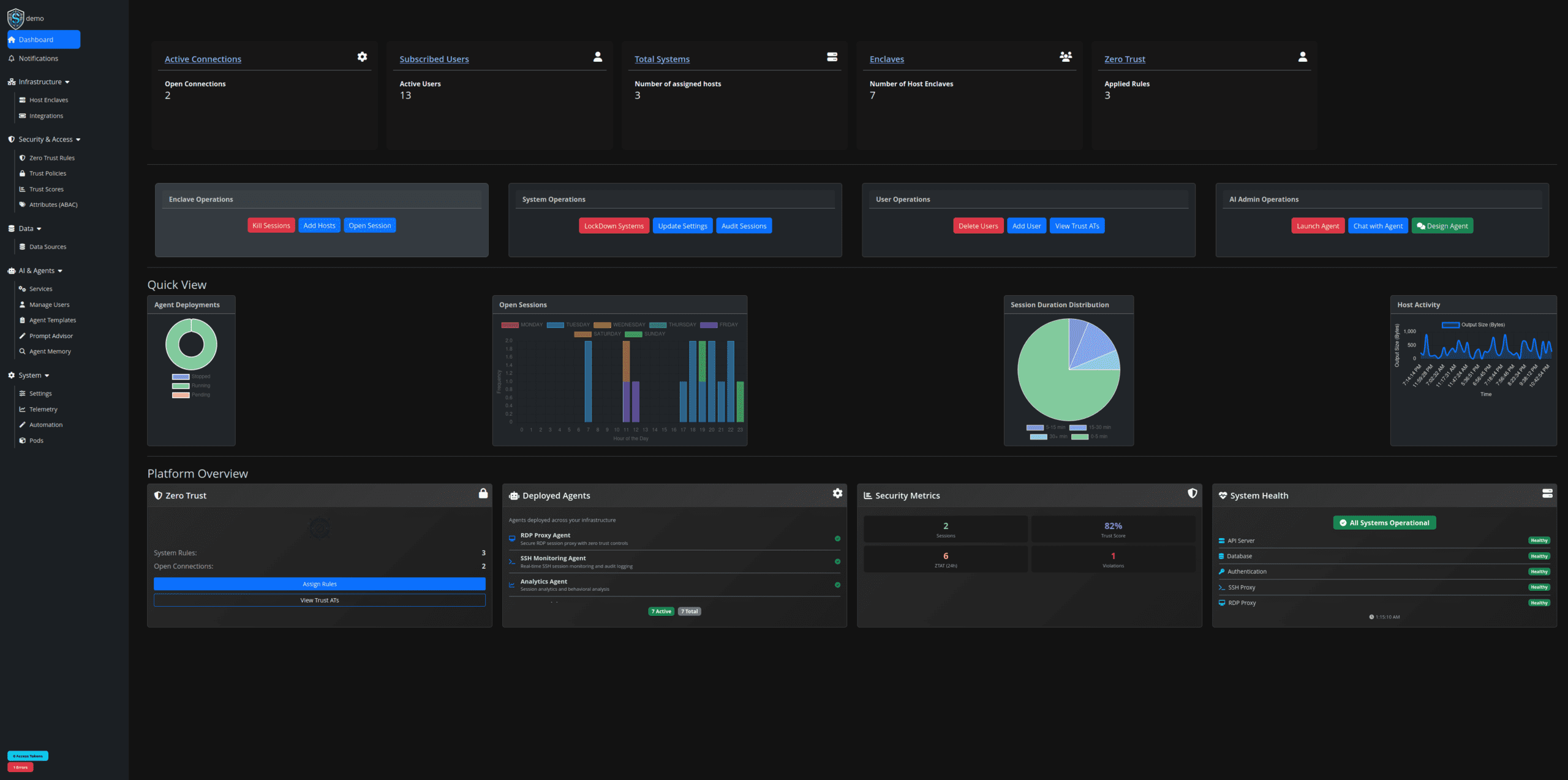





Feature Packed
Customizable
All features within Sentrius are Customizable, including views, rules, groups of hosts and their configurations
Supporting types of agents you can spin up agents and leverage external integrations seamlessly.
AI assisted
Agents assist in system management, performing security analysis of SSH or RDP Sessions, analyze RDP output, or develop automation. All done securely, without exposing tokens to agents, or comprimising system security
Setting the Ground Rules
You can customize rules, selecting pre-made intelligent rules or ones which you create through our simple API, that are enforced at the group level. Limiting rules enables you to control what admins can do at a much more granular level, even requiring Zero Trust Approval.
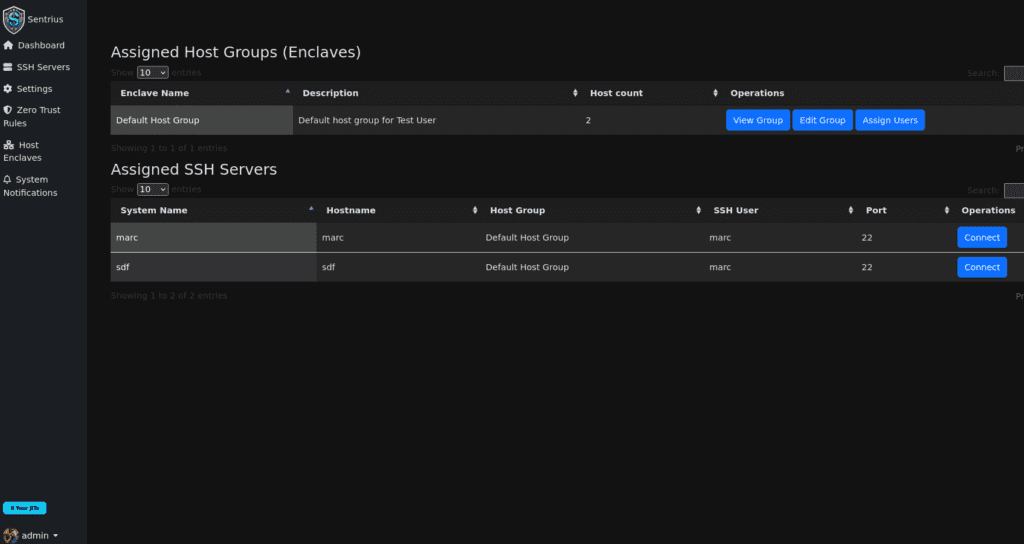
Active Monitoring
Rules integrate cleanly with our interface and we support real-time two party monitoring of audit sessions, allowing you to stop or pause sessions if something seems amiss. Anomaly detection enables you to actively intercept activities and score user activities in real time.
Custom Dashboard
Fully customizable dashboards enable you to select what users can see through our integrated RBAC/ABAC controls. All operations within the system are customizable and user views can vary with their selected responsibilities. Some users can edit/manage Zero Trust Rules, while some can only log into systems for which they have responsibility.
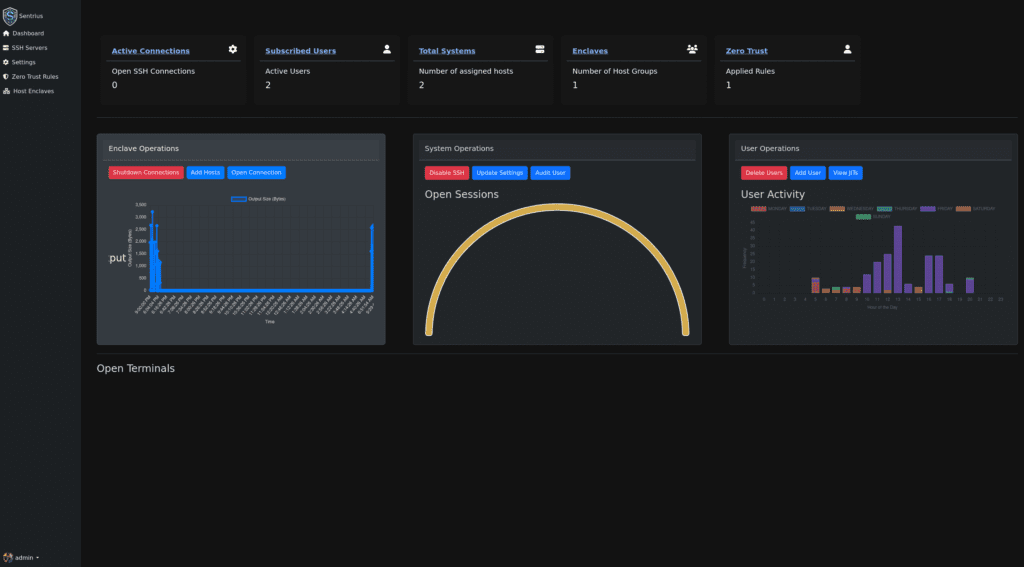
Simple Rule management
We make creating, managing, and applying rules of engagement simple. Not a replacement for ACLs, there are times when you want your SSH or RDP operations to be actively monitored. We enable that
We are Open Sourced. Check out our GitHub Repo!
